Command To Generate Ssh Key On Cisco Router
SSH or Secure Shell is basically a secured method of accessing and sending commands to your router’s CLI through a network connection; without having to plug a console cable directly. Unlike standard telnet that sends data in plain-text format, SSH uses encryption that will ensure confidentiality and integrity of the data. There are two versions of SSH, where SSH v2 is an improvement from v1 due to security holes that are found in v1. By default if we Enable SSH in Cisco IOS Router it will support both versions.
Sep 22, 2005 Learn how to configure SSH on your Cisco router. David Davis has the details. TR-Router(config)# crypto key generate rsa The name for the., use the ip. Jul 24, 2011 A quick intro on SSH, it expands to Secure Shell, listens on port 22, uses public key cryptography technique for encryption. Because SSH uses keys we need to generate one on the router. To connect using SSH from a windows system a third party software such as putty us needed, but for Linux users a SSH client is built into all distributions.
Enable SSH in Cisco IOS Router
How I create RSA key and enable SSH access in Cisco VG202, in a Cisco router I use the next commands(but in a VG not exists): conf t crypto key generate rsa modulus 1024 ip domain-name domain-name ip ssh version 2 ip ssh time-out 120 ip ssh authentication-retries 3 line vty 0 4 transport input telne. Run show crypto key mypubkey rsa to see if you do, in fact, have a key fully generated and registered under a non-default name. If there is, then you can tell the ssh process to use this key with ip ssh rsa keypair-name xxx. If the first command doesn't show anything useful then I'd say you can go ahead and generate a new key.
We can classify the process to into these 4 simple steps below:
1. Device preparation (setup hostname, domain name, username, and passwords)
2. Network preparation (IP addressing & routing)
3. Generate RSA key and activate SSH
4. Apply SSH transport for the vtys
The rest of this article will demonstrate the detailed configuration of each step mentioned above. Note that for first time configuration you will need to access your router directly using a console cable.
1. Device preparation
For the preparation step, you have to name your device and set the domain name. In this example we will use local database for credentials, so it is also mandatory to create at least one username and password for the router as SSH will not work without it. The example command to do it is as follows:
In this example we created the two username (‘admin’ and ‘monitor’) with different level of privilege. This will be explained in the verification section later.
For now, that’s all we need to configure. In the next step we are going to configure the network.
2. Network preparation
Network configuration may vary depends on the network topology that you’re working with. In this example, we are going to use a simple topology where one interface of the router connected to a standard Cisco switch with a PC attached to it. Static IP configuration has been given to the PC with the router Fa0/1 IP address as the gateway. We also have a management IP assigned to the loopback interface on the router. Please refer to the diagram and configuration below:
Assuming that all cables connected properly, now we’re going to give IP address the router Fa0/1 and loopback interface with the configurations below:
Generate Ssh Key Cmd
In this example topology, routing configuration is not required and we should have no problem with the IP address reachability. But it’s always a good idea to verify everything, in this case we would check if we can ping to the PC from the router’s loopback interface.
Based on the output above ping from router’s loopback interface to PC is working and surely the opposite ping will work too. Therefore, we can conclude that the network configurations are all good, and we can move on to our main focus in this article which is the SSH configuration.
Generate Ssh Key On Cisco Router
3. Generate RSA key and activate SSH
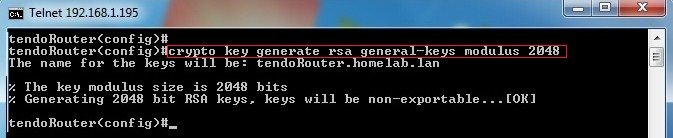
In this step we’re going to generate the RSA key that will be used by SSH to encrypt its data. You will need to specify the size of the key modulus. The higher the number, the stronger the encryption will become; but it will take more time to generate the key. In this example configuration below we’re using 1024 as the key modulus size, while the default size is 512.
/hibernate-cascade-generated-key-insert.html. After configuring as above, you will see a message similar to this:
This message indicates that SSH has been activated on the router. To verify it we can issue the command show ip ssh on the router and the output will be something like this:
You may be wondering why SSH version 1.99 is shown on the output instead of version 1 or version 2. The answer for that is because by default Cisco supports both SSH v1 and v2. The number 1.99 is to indicate backward compatibility.
However, according to security best practice, it is highly recommended to disable SSH v1. To do that, we can simply issue command below to disable the v1 backward compatibility.
After that, let’s verify once again:
Okay, as you can see on the output above it says version 2.0 (I feel more secure now!) and that means we are done with this step. Let’s move on the last step.
4. Apply SSH transport for the vtys
We already have SSH activated in the previous step. Now we only have two things left to do: apply SSH on the virtual terminal line, and then set login authentication method to use local username we created in the device preparation step.
We will achieve this using the command as in example below:
The command line vty 0 4 is used to specify the maximum number of virtual terminal sessions allowed on the router. In this example, we are allowing maximum 5 sessions (from session number 0 to session number 4) on the router.
The command transport input ssh will apply SSH to the virtual terminal line and also disable other methods like telnet. So that means after applying this command, SSH is the only method you can use to access the router.
The command login local is used to authenticate any login attempt against local username database, and remember that we’ve created two local username before (refer to step 1).
With this configuration, we’ve successfully Enable SSH on Cisco IOS Router.
Verification
We are now going to test accessing to our router using an SSH client software on the PC, in this example we’re using PuTTY. We specified the router loopback address 1.1.1.1 as the destination and SSH as the connection type.
We are then prompted to login, so we type username ‘admin’ and password ‘letmein123’ as we configured before (refer to step 1).
Great, we can now get in to the router CLI remotely using SSH! Remember that on step 1 we gave privilege level 15 to the username ‘admin’, therefore it can directly enter the privileged EXEC mode without an enable password (indicated by the ‘#’ sign next to the router hostname). What happens if we try to login using the ‘monitor’ username?
This username stays in the user EXEC mode (indicated by the ‘>’ sign next to the router hostname). On step 1, we didn’t assign any privilege level to this username therefore it is in default privilege level 1. It cannot do any configuration changes in user EXEC mode until it enters command enable and enter the password. Enable password is required for this to work, and that’s why we’ve configured it in step 1.
Managing the SSH session
Sometimes we would want to know who is currently logged in to our router. We can easily show the active users by issuing command show users on the router. The output will be something like this:
The output above shows that both username ‘admin’ and ‘monitor’ are currently logged in from the same IP address, since we only use one PC in this demonstration. However, you can see each one of them is having different session number. Username ‘admin’ has session number 0 and username ‘monitor’ has session number 1.
And if you notice, the asterisk (*) mark on the ‘admin’ username indicates that this command is executed from ‘admin’ session. You can disconnect any session from the privileged EXEC mode by issuing command clear line vty x where ‘x’ is the session number. In this example, we want to disconnect session from username ‘monitor’ and therefore we will use the command clear line vty 1. The output on ‘admin’ session will be like this:
We pressed enter key when asked for confirmation and got ‘OK’ as the result. With this command, we’ve successfully kicked out username ‘monitor’ from the SSH session, confirmed by the output from command below:
In this way you can enable SSH in Cisco IOS router.
You may also like -
Arranda Saputra
Command To Generate Ssh Key On Cisco Router Password
- Restore DHCP Server in Windows Server 2012 R2 - January 9, 2020
- Backup DHCP Server in Windows Server 2012 R2 - January 9, 2020
- Configure DHCP Reservation in Windows Server 2012 R2 - January 9, 2020
Privacy Overview
Command To Generate Ssh Key On Cisco Router Ip
Necessary cookies are absolutely essential for the website to function properly. This category only includes cookies that ensures basic functionalities and security features of the website. These cookies do not store any personal information.
Any cookies that may not be particularly necessary for the website to function and is used specifically to collect user personal data via analytics, ads, other embedded contents are termed as non-necessary cookies. It is mandatory to procure user consent prior to running these cookies on your website.