Generate Pre Shared Key Vpn
Introduction
Static key configurations offer the simplest setup, and are ideal for point-to-point VPNs or proof-of-concept testing.
The Pre-Shared Key (sometimes called shared secret) is basically a form of password for your VPN gateway which is set up on your device. The Pre-Shared Key is specific to your gateway and can be found in your device's configuration guide. VPN Tracker provides setup guides for all major gateway manufacturers. A VPN tunnel will be created with a server endpoint of 10.8.0.1 and a client endpoint of 10.8.0.2. Encrypted communication between client and server will occur over UDP port 1194, the default OpenVPN port. Generate a static key: Copy the static key to both client and server, over a. Solved: How do I locate the preshared key on an ASA firewall. Specifically, how do I find out what. is in the below configuration within my config file on my ASA firewall running 8.4(4)1? Aaa-server xxxxxxx (MGMT) host xxx.xxx.xxx.xxx timeout. Considerations about IPsec Pre-Shared Keys. 2015-01-19 Authentication, Crypto, IPsec/VPN Brute-Force. Generate a new/different PSK for every VPN tunnel. Use a password/passphrase generator for the creation of the PSK. Generate a long PSK with at least 30 chars, to resist a brute-force attack. Re: Updating VPN client pre-shared key Due to the mechanics of IKE and the preshared key, the concentrator won't allow the connection. I don't think you'd want someone to be able to establish a connection with a bad preshared key anyway.
Static Key advantages
RandomKeygen is a free mobile-friendly tool that offers randomly generated keys and passwords you can use to secure any application, service or device. KEY RandomKeygen - The Secure Password & Keygen Generator. How to generate secure pre-shared keys (PSK) for an IPSec VPN I build VPNs regularly, and one of the problems that comes up regularly is how to exchange PSK's. Some people are happy to exchange them over email, and others not (particularly because of ISO/IEC 27002).
- Simple Setup
- No X509 PKI (Public Key Infrastructure) to maintain
Static Key disadvantages
- Limited scalability — one client, one server
- Lack of perfect forward secrecy — key compromise results in total disclosure of previous sessions
- Secret key must exist in plaintext form on each VPN peer
- Secret key must be exchanged using a pre-existing secure channel
Simple Example
This example demonstrates a bare-bones point-to-point OpenVPN configuration. Wwe 2k19 serial key generator. Return auto generated key in sql. A VPN tunnel will be created with a server endpoint of 10.8.0.1 and a client endpoint of 10.8.0.2. Encrypted communication between client and server will occur over UDP port 1194, the default OpenVPN port.
Generate a static key:
Copy the static key to both client and server, over a pre-existing secure channel.
Server configuration file
Client configuration file
Firewall configuration
Make sure that:
- UDP port 1194 is open on the server, and
- the virtual TUN interface used by OpenVPN is not blocked on either the client or server (on Linux, the TUN interface will probably be called tun0 while on Windows it will probably be called something like Local Area Connection n unless you rename it in the Network Connections control panel).
Bear in mind that 90% of all connection problems encountered by new OpenVPN users are firewall-related.
Testing the VPN
Run OpenVPN using the respective configuration files on both server and client, changing myremote.mydomain in the client configuration to the domain name or public IP address of the server.
To verify that the VPN is running, you should be able to ping 10.8.0.2 from the server and 10.8.0.1 from the client.
Expanding on the Simple Example
Use compression on the VPN link
Add the following line to both client and server configuration files:
Make the link more resistent to connection failures
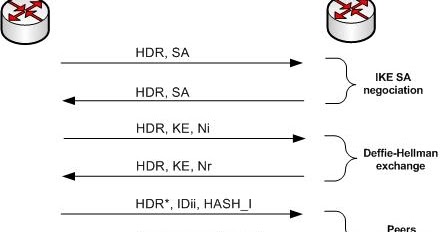
Ipsec Pre Shared Key
Deal with:
- keeping a connection through a NAT router/firewall alive, and
- follow the DNS name of the server if it changes its IP address.
Add the following to both client and server configuration files:
Run OpenVPN as a daemon (Linux/BSD/Solaris/MacOSX only)
Run OpenVPN as a daemon and drop privileges to user/group nobody.
Add to configuration file (client and/or server):
Allow client to reach entire server subnet
Suppose the OpenVPN server is on a subnet 192.168.4.0/24. Add the following to client configuration:
Sonicwall Vpn Pre Shared Key
Then on the server side, add a route to the server’s LAN gateway that routes 10.8.0.2 to the OpenVPN server machine (only necessary if the OpenVPN server machine is not also the gateway for the server-side LAN). Also, don’t forget to enable IP Forwarding on the OpenVPN server machine.