Generate A Public Key Javascript Rating: 6,5/10 5483 votes
- Generate A Public Key Javascript Free
- Public Key Example
- Javascript Generate Random Id
Generate A Public Key Javascript Free
Generating Keys. If you are going to connect to a remote host computer using public-key authentication, you will have to generate a key pair before connecting. Public-key authentication is based on the use of digital signatures. Each user creates a pair of key files.
About This Document>>
Installing SSH Tectia Client >>
Getting Started >>
Connecting to a Remote Host
Defining Quick Connect Options
Generating Keys
Key Generation Wizard
Key Generation - Start
Key Generation - Key Properties
Key Generation - Generation
Key Generation - Enter Passphrase
Key Generation - Finish
Enrolling Certificates >>
Uploading Your Public Key >>
Using Public-Key Authentication with SSH Accession Lite >>
Examples of Use
Configuring SSH Tectia Client >>
Connecting to a Remote Host Computer>>
Transferring Files>>
Tunneling Applications>>
GUI Reference>>
Troubleshooting >>
Command-Line Tools >>
|
Generating Keys If you are going to connect to a remote host computer using public-key authentication, you will have to generate a key pair before connecting. Auto primary key generator in hibernate. Public-key authentication is based on the use of digital signatures. Each user creates a pair of key files. One of these key files is the user's public key, and the other is the user's private key. The server knows the user's public key, and only the user has the private key. When the user tries to authenticate, the server checks for matching public keys and sends a challenge to the user end. The users are authenticated by signing the challenge using their private keys. Remember that your private key file is used to authenticate you. Never expose your private keys. If anyone else can access your private key file, they can attempt to log in to the remote host computer as you, and claim to be you. Therefore it is extremely important that you keep your private key file in a secure place and make sure that no one else has access to it. Do not use public-key authentication on a computer that is shared with other users. Generate keys only on your personal computer that no one else can access! Also note that if you are using the Windows roaming profiles functionality, your personal settings will be replicated with the roaming profile server. If you store your private keys in the default location (under the profile folder of your Windows user account) your private keys may be susceptible to a malicious user listening to the network traffic. Therefore the User Settings folder should not be a directory that is used in profile roaming. In order to use public-key authentication, you must first generate your own key pair. You can generate your own key files with the help of a built-in Key Generation wizard. You can also import existing keys on the Keys page of the Settings dialog. See Section Managing Keys. Key Generation Wizard Key Generation - Start Key Generation - Key Properties Key Generation - Generation Key Generation - Enter Passphrase Key Generation - Finish[Contents] [Index] [ Contact Information Support Feedback SSH Home Page SSH Products ] Copyright © 2010 SSH Communications Security Corp.
This software is protected by international copyright laws. All rights reserved.
Copyright Notice |
|
Public Key Example
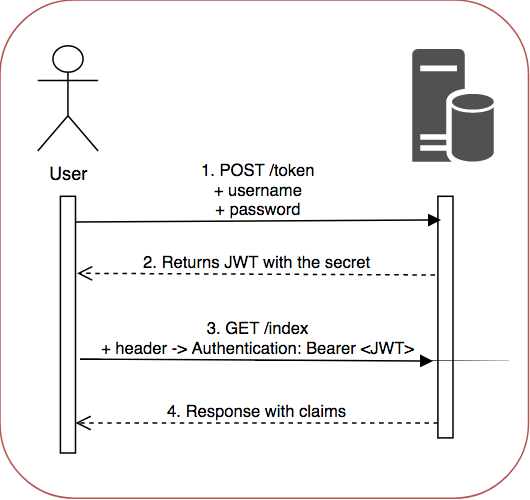
Javascript Generate Random Id
Many Git servers authenticate using SSH public keys. In order to provide a public key, each user in your system must generate one if they don’t already have one. This process is similar across all operating systems. First, you should check to make sure you don’t already have a key. Dec 10, 2017 Public Key Cryptography. In contrast to symmetric encryption, public key cryptography (asymmetric encryption) uses pairs of keys (one public, one private) instead of a single shared secret - public keys are for encrypting data, and private keys are for decrypting data. A public key is like an open box with an unbreakable lock. If someone wants. Jul 22, 2018 RSA Key Generation using Javascript. Shared-key and public-key encryption. But, I didn’t feel like I had a deep unedrstanding of public-key encryption. As I was reading this section of the. How to Generate a Public/Private Key Pair for Use With Solaris Secure Shell. Users must generate a public/private key pair when their site implements host-based authentication or user public-key authentication. For additional options, see the ssh-keygen(1) man page. Before You Begin. Creating a private/public key pair on Ubuntu Last updated: 04 Jun 2012. There are many reasons you might want to create a key pair on Linux, more specifically on Ubuntu. For more information about key pairs, see this. If your server is an Amazon EC2 Server Instance, you might want to look at more specific information here.

