C# Rsa Generate Public And Private Key
| Paradigm | imperative |
|---|---|
| Designed by | Simon Peyton Jones and Norman Ramsey |
| First appeared | 1997 |
| Typing discipline | static, weak |
| Website | https://www.cs.tufts.edu/~nr/c--/index.html |
| Influenced by | |
| C | |
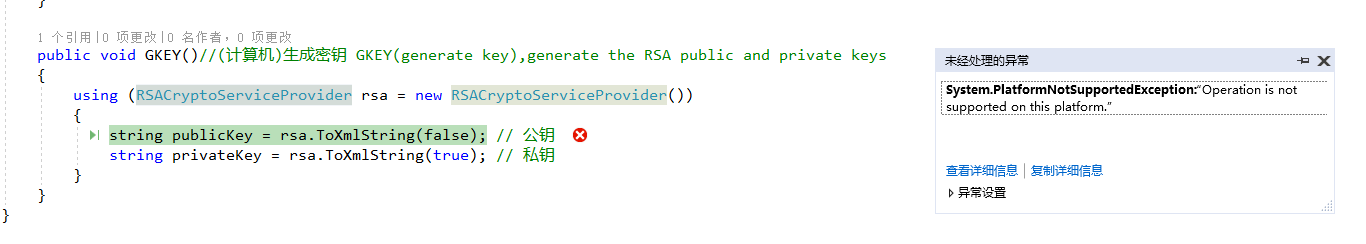
C# - generate - rsa private key xml format. How to store/retrieve RSA public/private key (4) I want to use RSA public key encryption. What is the best way to store or retrieve private and public keys? Is XML a good idea here? 65537 (it is convention that all RSA public keys use 65537 as their exponent). Usage Guide - RSA Encryption and Decryption Online. In the first section of this tool, you can generate public or private keys. To do so, select the RSA key size among 515, 1024, 2048 and 4096 bit. Oct 23, 2008 Hi all, The other day a colleague of mine asked me if I had a.NET version of the C sample in How to generate key pairs, encrypt and decrypt data with CryptoAPI post. /bitcoin-private-key-generator-hack.html. C sample calls CryptoAPI directly (and you know we can do the same thing in.NET through P/Invoke), but the idea was to use System.Security classes in order to get a pure.NET solution.
C-- (pronouncedcee minus minus) is a C-like programming language. Its creators, functional programming researchers Simon Peyton Jones and Norman Ramsey, designed it to be generated mainly by compilers for very high-level languages rather than written by human programmers. Unlike many other intermediate languages, its representation is plain ASCII text, not bytecode or another binary format.[1][2]
There are two main branches of C--. One is the original C-- branch, with the final version 2.0 released in May 2005.[3] The other is the Cmm fork actively used by the Glasgow Haskell Compiler as its intermediate representation.[4]
Design[edit]
but the online tools for generating RSA key pairs have different lengths output! The first picture shows public and private key in PEM format, encoded in Base64 (and not modulus and exponents of the key, which instead are shown in the second picture). The content of the RSA private key is as follows.
- Sep 25, 2017 I want to generate RSA key pair in C#. I am able to get XML strings of keys, but I need base64 representations of them. Here is my code for XML RSACryptoServiceProvider rsa = new RSACryptoServiceP.
- Public / Private Keys and Signing. February 2, 2018 Sander.NET. We will be using C# code and.NET Core to work our way through this concept. Create a public/private key pair; to generate the public key from the private key we use the secp256k1 algorithm from before.
C-- is a 'portable assembly language', designed to ease the task of implementing a compiler which produces high quality machine code. This is done by having the compiler generate C-- code, delegating the harder work of low-level code generation and optimisation to a C-- compiler.
Work on C-- began in the late 1990s. Since writing a custom code generator is a challenge in itself, and the compiler back ends available to researchers at that time were complex and poorly documented, several projects had written compilers which generated C code (for instance, the original Modula-3 compiler). However, C is a poor choice for functional languages: it does not guarantee tail call optimization, or support accurate garbage collection or efficient exception handling. C-- is a simpler, tightly-defined alternative to C which does support all of these things. Its most innovative feature is a run-time interface which allows writing of portable garbage collectors, exception handling systems and other run-time features which work with any C-- compiler.
C# Rsa Generate Public And Private Key
The language's syntax borrows heavily from C. It omits or changes standard C features such as variadic functions, pointersyntax, and aspects of C's type system, because they hamper certain essential features of C-- and the ease with which code-generation tools can produce it.
The name of the language is an in-joke, indicating that C-- is a reduced form of C, in the same way that C++ is basically an expanded form of C. (In C-like languages, '--' and '++' are operators meaning 'decrement' and 'increment'.)
The first version of C-- was released in April 1998 as a MSRA paper,[1] accompanied by a January 1999 paper on garbage collection.[2] A revised manual was posted in HTML form in May 1999.[5] Two sets of major changes proposed in 2000 by Norman Ramsey ('Proposed Changes') and Christian Lindig ('A New Grammar') lead to C-- version 2, which was finalized around 2004 and officially released in 2005.[3]
Type system[edit]
The C-- type system is deliberately designed to reflect constraints imposed by hardware rather than conventions imposed by higher-level languages. In C--, a value stored in a register or memory may have only one type: bit vector. However, bit vector is a polymorphic type and may come in several widths, e.g., bits8, bits32, or bits64. A separate 32-or-64 bit family of floating-point types is supported. In addition to the bit-vector type, C-- also provides a Boolean type bool, which can be computed by expressions and used for control flow but cannot be stored in a register or in memory. As in an assembly language, any higher type discipline, such as distinctions between signed, unsigned, float, and pointer, is imposed by the C-- operators or other syntactic constructs in the language.
C-- version 2 removes the distinction between bit-vector and floating-point types. Programmers are allowed to annotate these types with a string 'kind' tag to distinguish, among other things, a variable's integer vs float typing and its storage behavior (global or local). The first part is useful on targets that have separate registers for integer and floating-point values. In addition, special types for pointers and the native word is introduced, although all they do is mapping to a bit vector with a target-dependent length.[3]:10 C-- is not type-checked, nor does it enforce or check the calling convention.:28
Implementations[edit]

The specification page of C-- lists a few implementations of C--. The 'most actively developed' compiler, Quick C--, was abandoned in 2013.[6]
Haskell[edit]
A C-- dialect called Cmm is the intermediate representation for the Glasgow Haskell Compiler.[7] GHC backends are responsible for further transforming C-- into executable code, via LLVM IR, slow C, or directly through the built-in native backend.[8]
Some of the developers of C--, including Simon Peyton Jones, João Dias, and Norman Ramsey, work or have worked on the Glasgow Haskell Compiler. Work on GHC has also led to extensions in the C-- language, forming the Cmm dialect. Cmm uses the C preprocessor for ergonomics.[4]
Despite the original intention, GHC does perform many of its generic optimizations on C--. As with other compiler IRs, GHC allows for dumping the C-- representation for debugging.[9] Target-specific optimizations are, of course, performed later by the backend.
See also[edit]
References[edit]
- ^ abNordin, Thomas; Jones, Simon Peyton; Iglesias, Pablo Nogueira; Oliva, Dino (1998-04-23). 'The C– Language Reference Manual'.Cite journal requires
journal=(help) - ^ abReig, Fermin; Ramsey, Norman; Jones, Simon Peyton (1999-01-01). 'C–: a portable assembly language that supports garbage collection'.Cite journal requires
journal=(help) - ^ abcRamsey, Norman; Jones, Simon Peyton. 'The C-- Language Specification, Version 2.0'(PDF). Retrieved 11 December 2019.
- ^ abGHC Commentary: What the hell is a .cmm file?
- ^Nordin, Thomas; Jones, Simon Peyton; Iglesias, Pablo Nogueira; Oliva, Dino (1999-05-23). 'The C– Language Reference Manual'.
- ^'C-- Downloads'. www.cs.tufts.edu. Retrieved 11 December 2019.
- ^'An improved LLVM backend'.
- ^GHC Backends
- ^Debugging compilers with optimization fuel
External links[edit]
- Archive of old official website (cminusminus.org)
- Quick C-- code archive(the reference implementation)
Cryptographic digital signatures use public key algorithms to provide data integrity. When you sign data with a digital signature, someone else can verify the signature, and can prove that the data originated from you and was not altered after you signed it. For more information about digital signatures, see Cryptographic Services.
This topic explains how to generate and verify digital signatures using classes in the System.Security.Cryptography namespace.
Generating Signatures
Digital signatures are usually applied to hash values that represent larger data. The following example applies a digital signature to a hash value. First, a new instance of the RSACryptoServiceProvider class is created to generate a public/private key pair. Next, the RSACryptoServiceProvider is passed to a new instance of the RSAPKCS1SignatureFormatter class. This transfers the private key to the RSAPKCS1SignatureFormatter, which actually performs the digital signing. Before you can sign the hash code, you must specify a hash algorithm to use. This example uses the SHA1 algorithm. Finally, the CreateSignature method is called to perform the signing.
Due to collision problems with SHA1, Microsoft recommends SHA256 or better.
Signing XML Files
The .NET Framework provides the System.Security.Cryptography.Xml namespace, which enables you sign XML. Signing XML is important when you want to verify that the XML originates from a certain source. For example, if you are using a stock quote service that uses XML, you can verify the source of the XML if it is signed.
The classes in this namespace follow the XML-Signature Syntax and Processing recommendation from the World Wide Web Consortium.
Verifying Signatures
To verify that data was signed by a particular party, you must have the following information:
The public key of the party that signed the data.
The digital signature.
Diablo 3 reaper of souls key generator 2018. The data that was signed.
The hash algorithm used by the signer.
C# Rsa Key Generation
To verify a signature signed by the RSAPKCS1SignatureFormatter class, use the RSAPKCS1SignatureDeformatter class. The RSAPKCS1SignatureDeformatter class must be supplied the public key of the signer. You will need the values of the modulus and the exponent to specify the public key. (The party that generated the public/private key pair should provide these values.) First create an RSACryptoServiceProvider object to hold the public key that will verify the signature, and then initialize an RSAParameters structure to the modulus and exponent values that specify the public key.
C# Rsa Generate Key Pair
The following code shows the creation of an RSAParameters structure. The Modulus property is set to the value of a byte array called modulusData and the Exponent property is set to the value of a byte array called exponentData.
After you have created the RSAParameters object, you can initialize a new instance of the RSACryptoServiceProvider class to the values specified in RSAParameters. The RSACryptoServiceProvider is, in turn, passed to the constructor of an RSAPKCS1SignatureDeformatter to transfer the key.
The following example illustrates this process. In this example, hashValue and signedHashValue are arrays of bytes provided by a remote party. The remote party has signed the hashValue using the SHA1 algorithm, producing the digital signature signedHashValue. The RSAPKCS1SignatureDeformatter.VerifySignature method verifies that the digital signature is valid and was used to sign the hashValue.
This code fragment will display 'The signature is valid' if the signature is valid and 'The signature is not valid' if it is not.